Annual Gift Guide, Holiday Travel Surveillance, Litigation Review, Digital Forensics Discovery (Part II) & More
Vol. 3, Issue 12

December 5, 2022
Welcome to Decrypting a Defense, the monthly newsletter of the Legal Aid Society’s Digital Forensics Unit. In this issue, Diane Akerman shares her 2022 Digital Elf on a Shelf gift guide. Jerome Greco warns of surveillance when traveling for the holidays. Benjamin Burger reviews some of the legal decisions the Digital Forensics Unit worked on this year. Finally, Allison Young presents the second part of a series on digital forensics discovery.
The Digital Forensics Unit of the Legal Aid Society was created in 2013 in recognition of the growing use of digital evidence in the criminal legal system. Consisting of attorneys and forensic analysts and examiners, the Unit provides support and analysis to the Criminal, Juvenile Rights, and Civil Practices of the Legal Aid Society.
Digital Elf On The Shelf: A Holiday Gift Guide
Diane Akerman, Digital Forensics Staff Attorney
It’s that time of year again! The holidays are here! Time to enjoy food and drink in the company of your loved ones! To attend awkward holiday parties with coworkers! To find just the right gift for the office White Elephant you somehow got dragged into again, or the family Secret Santa you thought you avoided by deleting Whatsapp! (Good try!)
What do you get that coworker or relative who you just don’t like? That family member who you just don’t agree with? Behold, our 2022 Digital Elf On The Shelf, this year’s best privacy violating gifts.
Amazon Ring Always Home Cam: An obvious first on the list this year (and every year forever), the preeminent product in the Bezos Surveillance State is back…in drone form! You already know about the Ring’s friendly relationship with law enforcement and their loosey-goosey security practices, but did you know they also record audio? With illegal wiretaps now a built-in feature, is there anything the Ring can’t do?
Glow: Glow provides an array of popular apps including Glow, Nurture, Baby, and Eve by Glow so you can be confident that there will be one available to suit the needs of your gift recipient. Glow is sure to share their data with a whole slew of third-party companies and developers, fail to safeguard their health data, and happily turn over information to law enforcement even without a warrant. Be sure to laugh heartily when the recipient asks you about HIPAA.
Dating Apps: Abandon all hope privacy ye who enter tinder here! Or Hinge, or OKCupid because they are all owned by the Match Group. Great news! Their privacy policy no longer has the alarming proclamation that they “do not promise, and you should not expect, that your personal information will always remain secure.” Bad news: you might be looking for love, but they are still looking to monetize your data. As if being on a dating app wasn’t bad enough.
Mirror: The holidays also usher in New Years Resolutions, and with them, an endless array of deals on local gyms and fitness equipment. Well, what if all that but make it super creepy? Work out in the privacy of your own home with no real guarantee that audio and video isn’t being saved somewhere! Consult with a virtual personal trainer and hope that information won’t get fed directly to Facebook with your name on it. I’m sure it’s fine, it comes with a lens cap.
Just remember to sign the card: “If you aren’t doing anything wrong, there’s nothing to hide!”
Happy Holidays from the Digital Forensics Unit, who are literally begging you to stop snitching on yourself. Or at least, use two-factor-authentication. Please.
He Sees You When You’re Sleeping and He Knows Your License Plate
Jerome D. Greco, Digital Forensics Supervising Attorney
Santa Claus is coming to town. Musicians have prophesied (and warned of) his annual return for decades, including Harry Reser, Bing Crosby, The Supremes, The Jackson 5, Bruce Springsteen, Mariah Carey, and so many others.
Santa delivers gifts to (some) children all over the world, magically making the trip in one night. But most impressive (or terrifying) is that he uses the data he has gathered over the year to determine where each child lives and whether they receive toys or coal. Commercial competitors have coveted his network of data collection for generations. Last year, rumors abounded about Amazon’s unsuccessful merger with Santa’s workshop. The likely sticking point was the unionization of the working elves. Yet, even Santa has nothing on the U.S. government. After all, every year since 1955 he has failed to escape NORAD’s all watchful eye. Father Christmas has met his match in Big Brother.
The removal of most COVID restrictions has reinvigorated the time-honored tradition of spending many frustrating hours traveling to visit family so you can argue about politics celebrate together. With each mode of transportation comes its own surveillance risks and invasions of privacy. If you plan on driving, automated license plate readers and electronic toll collection systems scattered across the country keep track of your vehicle’s locations. If you intend on flying, the TSA continues to test new ways to invade your privacy.
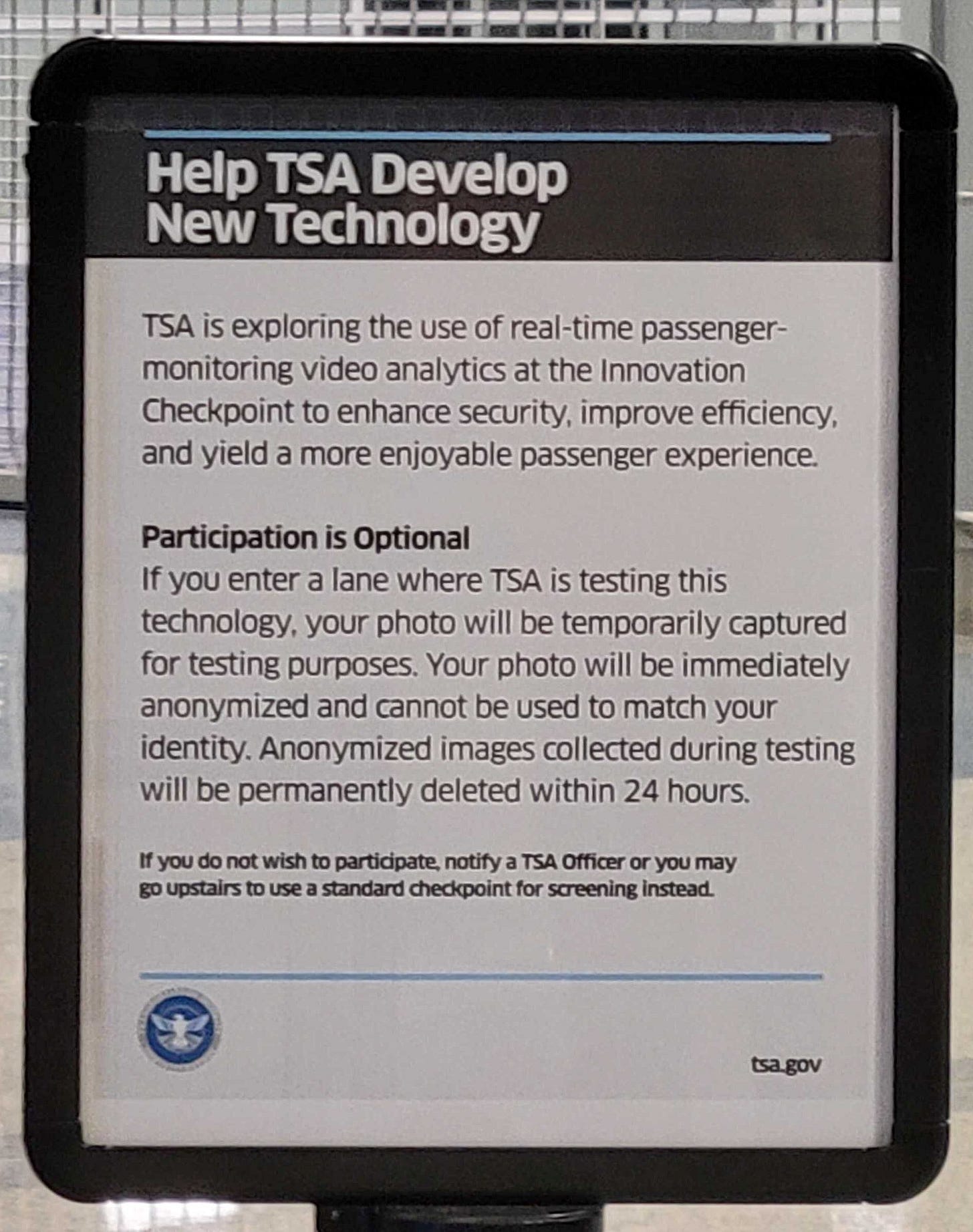
The TSA has recently been testing facial recognition technology as a replacement for human employees’ ID verifications. There are many issues that arise out of this program. For example, it is not mandatory, but it forces passengers to opt-out, rather than opt-in. From personal experience, I know just how difficult it can be to opt-out. This summer I was checking-in at Harry Reid International Airport in Las Vegas for a flight home. I was stuck in a long line when a TSA agent removed one of the barriers and directed everyone in that part of the line to a different check-in area one level down. We were not given an option to refuse the directive nor was any other information conveyed to us. After following their directions, I then waited in a shorter line, but it was not until I made it to the front that I saw the small signs depicted in the above photo, describing the new “video analytics” technology they wanted to test on us. I did not want to take part in this new program and was forced to return to my original location upstairs. I had to restart my wait from the back of my original line. Thankfully, I had enough time to do so, but it appeared that most people just went through with it. The cost of anyone’s refusal to take part in this “optional” program was to have their time wasted and potentially miss their flights.
Law enforcement continuously takes advantage of people’s fears and their desire for convenience to justify invading our privacy and diminishing our rights. Do not let either your holiday cheer or holiday stress distract you from the surveillance state. Stay vigilant and close your chimneys.
In the Courts
In Review
Benjamin Burger, Digital Forensics Staff Attorney
The Legal Aid Society’s Digital Forensics Unit takes an active role litigating cases in New York State. In conjunction with the trial attorneys in the Criminal Defense Practice, we file motions to controvert digital search warrants and Frye motions to preclude unproven scientific testimony. This year we also litigated FOIL requests with state and city agencies, pursued an Article 78 in New York Supreme Court, and filed an amicus curiae brief in the New York Court of Appeals. The three summaries below are just some of the many cases litigated with the assistance of the Digital Forensics Unit.
People v. Rodriguez, 38 N.Y.3d 151 (2022)
This Court of Appeals case concerned the proper standard for authenticating text messages [PDF] - more specifically, screenshots of text messages where the “original” messages had been deleted. The Legal Aid Society filed an amicus brief explaining to the Court that from a forensic perspective, screenshots of text messages are unreliable and subject to manipulation. Unfortunately, the Court of Appeals found that the screenshots were admissible under the same authentication standard that already exists for photographs. Citing to People v. Price, 29 NY.3d 472 (2017), the Court observed that the screenshots were properly authenticated by a witness who testified that they “fairly and accurately represented text messages sent to and from [the] defendant’s phone.” Rodriguez, 38 N.Y.3d at 155. Rodriguez fails to consider the myriad ways that digital messages like texts can be altered or faked. Instead, the Court clarified that when it comes to admitting screenshots, authentication alone will not bar admissibility.
People v. Gonzalez, 74 Misc.3d 1140 (N.Y. Sup. Ct. 2022)
In Gonzalez, the Court granted motions to controvert three search warrants authorizing the search of two cell phones and the seizure of historical cell site location information. The prosecution originally secured a search warrant for the defendant’s phone in August 2016. This search warrant only sought data related to the date of an alleged assault. However, law enforcement was not able to gain access to the device. A year later, the prosecution acquired a second search warrant, which authorized a search of the same cell phone with the use of Cellebrite forensic tools. Although this search warrant incorporated the prior 2016 warrant, it sought a broader data range of over eight-months. The New York County Supreme Court ruled that this second search warrant was unconstitutionally broad. Gonzalez, 74 Misc.3d at 1143. As the second warrant did not include additional facts justifying the more expansive search, “the time frame and unfettered ‘locations’ for the search failed to satisfy the particularity requirement under the Fourth Amendment.” The Court suppressed any evidence seized pursuant to the second warrant and any fruits of the suppressed evidence - which included the two additional search warrants. Gonzalez represents a success in educating courts on the need to examine digital device search warrants. Warrants that allow for the seizure and search of the entirety of a device’s data are often overbroad and lack particularity.
People v. Gomez, 76 Misc.3d 1230(A) (N.Y. Sup. Ct. 2022)
Another Supreme Court decision out of Manhattan granted a pre-trial hearing partially to determine if the New York Police Department’s use of facial recognition software to identify as suspect created an unduly suggestive identification procedure. Generally, when NYPD’s Facial Identification Section uses facial recognition technology to identify a person, they send the investigating officer a “Potential Match Report” which states that a facial recognition “match” is not probable cause and cannot be used as the sole basis for an arrest. NYPD will then conduct an identification procedure - usually a photo array - with a witness. The probable cause for the arrest is technically based on the second identification, not on the initial facial recognition match. In Gomez, a police officer who had previously arrested the defendant made the second identification. Differentiating People v. Gee, 286 A.D.2d 62 (4th Dept. 2001), the Court ordered a hearing to determine whether the second identification procedure was suggestive, as it appeared “more to be a confirmatory procedure than an attempt to pinpoint a suspect, as in Gee.” Gomez, 76 Misc. 3d 1230(A), *1 (N.Y. Sup. Ct. 2022). NYPD’s use of controversial facial recognition technology has normally been shielded from in-court litigation. Gomez shows that its use can be challenged under the rubric identification procedures.
Ask an Analyst
The following article is Part Two of a special three-part series on digital forensics discovery in criminal cases. Part One addressed call detail records from wireless phone providers. Part Two covers portable reports and screenshots. Part Three will be included in a future Decrypting a Defense Newsletter.
Allison Young, Digital Forensics Analyst
Part 2: Maybe Things Aren’t What They Look Like 🤔
Welcome to Part 2 of the Discovery and Digital Forensics series. Last month, I covered cell site records and issues mapping them. This month, I’ll cover portable reports and screenshots (and why you shouldn’t rely on them).
Portable Reports (AXIOM and Cellebrite)
Magnet AXIOM and Cellebrite Physical Analyzer are two well-known and well-used software tools that can produce portable reports. Portable reports are software programs that display analyzed digital evidence similarly to how an expert might view the data in the full versions of these tools.
The original source data, such as a phone extraction or computer “image” (exact copy), is not necessarily included with these reports. It can be difficult or impossible to confirm whether all relevant communications, photos, or other evidence is included in the report.

A report is limited by the automated capabilities of the tools – manual analysis by an expert or future updates to the software could find more information at a future date. Without the original source data that the report was prepared from, you cannot take advantage of new technology or additional expert review.
These tools can also prepare PDF and spreadsheet reports affected by the same issues (data exclusion), although it is less common to see these reports incorrectly referred to as “a full copy of the extraction.”
Keep in mind that while a report may be large (for instance, 1-10 gigabytes), the original copy of the evidence is often larger (15 gigabytes – 2 terabytes, or 2000 gigabytes)! For context, one side of a DVD holds less than 5 gigabytes.
Takeaways:
Reports are never as good as the original data
Reports are NOT the “full extraction”
You may receive reports more often after asking for a full extraction due to the large size of device (phone, computer, etc.) preservations
Screenshots
If you receive screenshots, such as one depicting a conversation between a client and a complaining witness, you should consider whether the image has been manipulated or whether there is missing context. A screenshot of texts could display a contact name like “John Smith,” but be associated with a phone number used by another individual.
A digital forensic expert may identify metadata in the screenshot that refutes a witness’s timeline. If that metadata is not available or inconclusive, a forensic extraction could confirm the presence or lack of messages depicted in a screenshot.

Takeaways:
Screenshots are easily faked
Screenshots are missing context (such as prior messages or the identity of the participants)
Upcoming Events
December 5, 2022 (Today)
Unpacking the White House blueprint for an AI Bill of Rights (Brookings Institute) (Virtual and Washington, D.C.)
December 7, 2022
Tech & Society Salon: The Home Surveillance State (STOP) (Virtual)
December 9, 2022
Putting the Brain on Trial: Cognitive Bias in Forensic Decisions (ABA) (Virtual)
December 15, 2022
Meta What? Everything You Wanted to Know About Metadata But Were Too Afraid to Ask (LAS Digital Forensics Unit & NYCBA) (Virtual) (Legal Aid Society Registration) (Non-Legal Aid Society Registration)
December 16, 2022
Evidentiary and Policy Questions about Police Body Cameras (ABA) (Virtual)
March 11-18, 2023
Open Data Week 2023 (Various Locations in NYC)
April 17-19, 2023
Magnet User Summit (Magnet Forensics) (Nashville, TN)
April 27-29, 2023
16th Annual Forensic Science & The Law Seminar (NACDL) (Las Vegas, NV)
Small Bytes
For Sex Traffickers, Jack Dorsey’s Cash App Is ‘King’ (Forbes)
Montana votes to approve amendment requiring warrants for data (Washington Examiner)
The Quiet Invasion of ‘Big Information’ (Wired)
Anxieties about crime are undoing the gains of the anti-surveillance movement in cities across the United States (Coda Story)
Internal Documents Show How Close the F.B.I. Came to Deploying Spyware (The New York Times)
NYPD spent $3 billion on surveillance but critics say details are vague despite new disclosure law (New York Daily News)
Mental Health Apps Are Not Keeping Your Data Safe (Scientific American)
A Peek Inside the FBI’s Unprecedented January 6 Geofence Dragnet (Wired)
The State Police Want to Crack Your Phone (New York Focus)
What to Know Now That the N.Y.P.D. Is on Amazon’s Neighborhood Watch App (The New York Times)







